A brand new marketing campaign is focusing on corporations in Taiwan with malware often known as Winos 4.0 as a part of phishing emails masquerading because the nation’s Nationwide Taxation Bureau.
The marketing campaign, detected final month by Fortinet FortiGuard Labs, marks a departure from earlier assault chains which have leveraged malicious game-related functions.
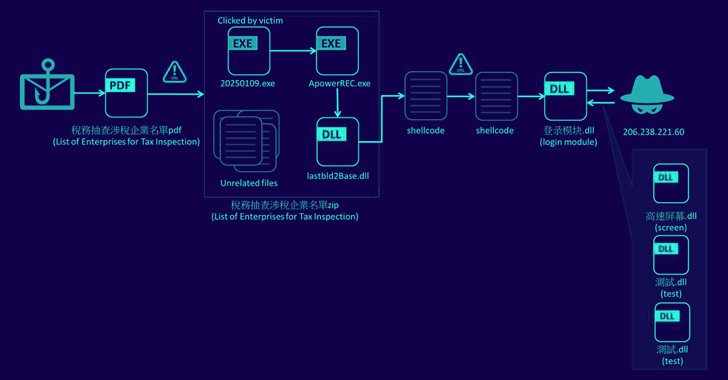
“The sender claimed that the malicious file hooked up was a listing of enterprises scheduled for tax inspection and requested the receiver to ahead the data to their firm’s treasurer,” safety researcher Pei Han Liao mentioned in a report shared with The Hacker Information.
The attachment mimics an official doc from the Ministry of Finance, urging the recipient to obtain the record of enterprises scheduled for tax inspection.
However in actuality, the record is a ZIP file containing a malicious DLL (“lastbld2Base.dll”) that lays the groundwork for the following assault stage, resulting in the execution of shellcode that is accountable for downloading a Winos 4.0 module from a distant server (“206.238.221[.]60”) for gathering delicate knowledge.
The part, described as a login module, is able to taking screenshots, logging keystrokes, altering clipboard content material, monitoring linked USB units, working shellcode, and allowing the execution of delicate actions (e.g., cmd.exe) when safety prompts from Kingsoft Safety and Huorong are displayed.
Fortinet mentioned it additionally noticed a second assault chain that downloads a web based module that may seize screenshots of WeChat and on-line banks.

It is price noting that the intrusion set distributing the Winos 4.0 malware has been assigned the monikers Void Arachne and Silver Fox, with the malware additionally overlapping with one other distant entry trojan tracked as ValleyRAT.
“They’re each derived from the identical supply: Gh0st RAT, which was developed in China and open-sourced in 2008,” Daniel dos Santos, Head of Safety Analysis at Forescout’s Vedere Labs, advised The Hacker Information.
“Winos and ValleyRAT are variations of Gh0st RAT attributed to Silver Fox by completely different researchers at completely different closing dates. Winos was a reputation generally utilized in 2023 and 2024 whereas now ValleyRAT is extra generally used. The software is continually evolving, and it has each native Trojan/RAT capabilities in addition to a command-and-control server.”
ValleyRAT, first recognized in early 2023, has been lately noticed utilizing faux Chrome websites as a conduit to contaminate Chinese language-speaking customers. Comparable drive-by obtain schemes have additionally been employed to ship Gh0st RAT.
Moreover, Winos 4.0 assault chains have integrated what’s known as a CleverSoar installer that is executed by way of an MSI installer package deal distributed as faux software program or gaming-related functions. Additionally dropped alongside Winos 4.0 by way of CleverSoar is the open-source Nidhogg rootkit.
“The CleverSoar installer […] checks the consumer’s language settings to confirm if they’re set to Chinese language or Vietnamese,” Rapid7 famous in late November 2024. “If the language will not be acknowledged, the installer terminates, successfully stopping an infection. This habits strongly means that the menace actor is primarily focusing on victims in these areas.”

The disclosure comes because the Silver Fox APT has been linked to a brand new marketing campaign that leverages trojanized variations of Philips DICOM viewers to deploy ValleyRAT, which is then used to drop a keylogger, and a cryptocurrency miner on sufferer computer systems. Notably, the assaults have been discovered to make use of a weak model of the TrueSight driver to disable antivirus software program.
“This marketing campaign leverages trojanized DICOM viewers as lures to contaminate sufferer techniques with a backdoor (ValleyRAT) for distant entry and management, a keylogger to seize consumer exercise and credentials, and a crypto miner to use system sources for monetary acquire,” Forescout mentioned.