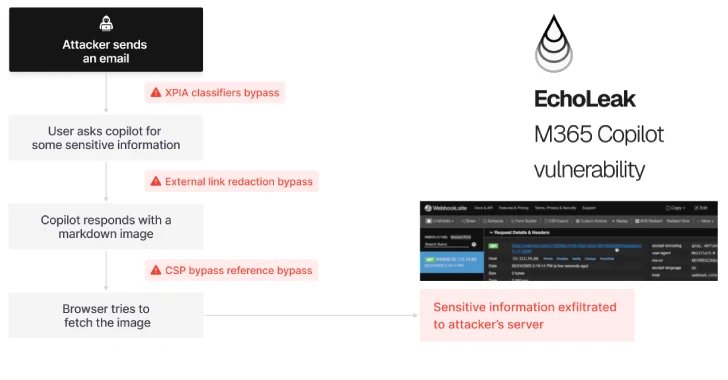
A novel assault approach named EchoLeak has been characterised as a “zero-click” synthetic intelligence (AI) vulnerability that permits dangerous actors to exfiltrate delicate knowledge from Microsoft 365 (M365) Copilot’s context sans any person interplay.
The critical-rated vulnerability has been assigned the CVE identifier CVE-2025-32711 (CVSS rating: 9.3). It requires no buyer motion and has been already addressed by Microsoft. There isn’t any proof that the shortcoming was exploited maliciously within the wild.
“AI command injection in M365 Copilot permits an unauthorized attacker to reveal info over a community,” the corporate stated in an advisory launched Wednesday. It has since been added to Microsoft’s Patch Tuesday record for June 2025, taking the full variety of fastened flaws to 68.
Purpose Safety, which found and reported the problem, stated it is an occasion of a giant language mannequin (LLM) Scope Violation that paves the best way for oblique immediate injection, resulting in unintended habits.
LLM Scope Violation happens when an attacker’s directions embedded in untrusted content material, e.g., an e mail despatched from exterior a corporation, efficiently tips the AI system into accessing and processing privileged inner knowledge with out specific person intent or interplay.
“The chains permit attackers to mechanically exfiltrate delicate and proprietary info from M365 Copilot context, with out the person’s consciousness, or counting on any particular sufferer habits,” the Israeli cybersecurity firm stated. “The result’s achieved regardless of M365 Copilot’s interface being open solely to group staff.”
In EchoLeak’s case, the attacker embeds a malicious immediate payload inside markdown-formatted content material, like an e mail, which is then parsed by the AI system’s retrieval-augmented technology (RAG) engine. The payload silently triggers the LLM to extract and return non-public info from the person’s present context.

The assault sequence unfolds as follows –
- Injection: Attacker sends an innocuous-looking e mail to an worker’s Outlook inbox, which incorporates the LLM scope violation exploit
- Person asks Microsoft 365 Copilot a business-related query (e.g., summarize and analyze their earnings report)
- Scope Violation: Copilot mixes untrusted attacked enter with delicate knowledge to LLM context by the Retrieval-Augmented Technology (RAG) engine
- Retrieval: Copilot leaks the delicate knowledge to the attacker through Microsoft Groups and SharePoint URLs
Importantly, no person clicks are required to set off EchoLeak. The attacker depends on Copilot’s default habits to mix and course of content material from Outlook and SharePoint with out isolating belief boundaries – turning useful automation right into a silent leak vector.
“As a zero-click AI vulnerability, EchoLeak opens up in depth alternatives for knowledge exfiltration and extortion assaults for motivated menace actors,” Purpose Safety stated. “In an ever-evolving agentic world, it showcases the potential dangers which are inherent within the design of brokers and chatbots.”

“The assault leads to permitting the attacker to exfiltrate probably the most delicate knowledge from the present LLM context – and the LLM is getting used in opposition to itself in ensuring that the MOST delicate knowledge from the LLM context is being leaked, doesn’t depend on particular person habits, and will be executed each in single-turn conversations and multi-turn conversations.”
EchoLeak is particularly harmful as a result of it exploits how Copilot retrieves and ranks knowledge – utilizing inner doc entry privileges – which attackers can affect not directly through payload prompts embedded in seemingly benign sources like assembly notes or e mail chains.
MCP and Superior Software Poisoning
The disclosure comes as CyberArk disclosed a device poisoning assault (TPA) that impacts the Mannequin Context Protocol (MCP) normal and goes past the device description to increase it throughout the complete device schema. The assault approach has been codenamed Full-Schema Poisoning (FSP).
“Whereas a lot of the consideration round device poisoning assaults has targeted on the outline discipline, this vastly underestimates the opposite potential assault floor,” safety researcher Simcha Kosman stated. “Each a part of the device schema is a possible injection level, not simply the outline.”
 |
| MCP device poisoning assaults (Credit score: Invariant Labs) |
The cybersecurity firm stated the issue is rooted in MCP’s “essentially optimistic belief mannequin” that equates syntactic correctness to semantic security and assumes that LLMs solely cause over explicitly documented behaviors.
What’s extra, TPA and FSP might be weaponized to stage superior device poisoning assaults (ATPA), whereby the attacker designs a device with a benign description however shows a faux error message that tips the LLM into accessing delicate knowledge (e.g., SSH keys) to be able to deal with the purported problem.
“As LLM brokers grow to be extra succesful and autonomous, their interplay with exterior instruments by way of protocols like MCP will outline how safely and reliably they function,” Kosman stated. “Software poisoning assaults — particularly superior kinds like ATPA — expose crucial blind spots in present implementations.”
That is not all. On condition that MCP allows AI brokers (or assistants) to work together with numerous instruments, providers, and knowledge sources in a constant method, any vulnerability within the MCP client-server structure might pose critical safety dangers, together with manipulating an agent into leaking knowledge or executing malicious code.
That is evidenced in a not too long ago disclosed crucial safety flaw within the standard GitHub MCP integration, which, if efficiently exploited, might permit an attacker to hijack a person’s agent through a malicious GitHub problem, and coerce it into leaking knowledge from non-public repositories when the person prompts the mannequin to “check out the problems.”
“The problem incorporates a payload that will probably be executed by the agent as quickly because it queries the general public repository’s record of points,” Invariant Labs researchers Marco Milanta and Luca Beurer-Kellner stated, categorizing it as a case of a poisonous agent movement.
That stated, the vulnerability can’t be addressed by GitHub alone by way of server-side patches, because it’s extra of a “basic architectural problem,” necessitating that customers implement granular permission controls to make sure that the agent has entry to solely these repositories it must work together with and repeatedly audit interactions between brokers and MCP programs.
Make Approach for the MCP Rebinding Assault
The fast ascent of MCP because the “connective tissue for enterprise automation and agentic purposes” has additionally opened up new assault avenues, reminiscent of Area Identify System (DNS) rebinding, to entry delicate knowledge by exploiting Server-Despatched Occasions (SSE), a protocol utilized by MCP servers for real-time streaming communication to the MCP purchasers.
DNS rebinding assaults entail tricking a sufferer’s browser into treating an exterior area as if it belongs to the inner community (i.e., localhost). These assaults, that are engineered to bypass same-origin coverage (SOP) restrictions, are triggered when a person visits a malicious website arrange by the attacker through phishing or social engineering.
“There’s a disconnect between the browser safety mechanism and networking protocols,” GitHub’s Jaroslav Lobacevski stated in an explainer on DNS rebinding printed this week. “If the resolved IP deal with of the net web page host modifications, the browser would not take it into consideration and treats the webpage as if its origin did not change. This may be abused by attackers.”
This habits primarily permits client-side JavaScript from a malicious website to bypass safety controls and goal different units on the sufferer’s non-public community that aren’t uncovered to the general public web.
 |
| MCP rebinding assault |
The MCP rebinding assault takes benefit of an adversary-controlled web site’s means to entry inner assets on the sufferer’s native community in order to work together with the MCP server working on localhost over SSE and in the end exfiltrate confidential knowledge.
“By abusing SSE’s long-lived connections, attackers can pivot from an exterior phishing area to focus on inner MCP servers,” the Straiker AI Analysis (STAR) staff stated in an evaluation printed final month.
It is price noting that SSE has been deprecated as of November 2024 in favor of Streamable HTTP owing to the dangers posed by DNS rebinding assaults. To mitigate the specter of such assaults, it is suggested to implement authentication on MCP Servers and validate the “Origin” header on all incoming connections to the MCP server to make sure that the requests are coming from trusted sources.