A novel assault approach could possibly be weaponized to rope hundreds of public area controllers (DCs) around the globe to create a malicious botnet and use it to conduct energy distributed denial-of-service (DDoS) assaults.
The method has been codenamed Win-DDoS by SafeBreach researchers Or Yair and Shahak Morag, who introduced their findings on the DEF CON 33 safety convention right now.
“As we explored the intricacies of the Home windows LDAP shopper code, we found a major flaw that allowed us to control the URL referral course of to level DCs at a sufferer server to overwhelm it,” Yair and Morag mentioned in a report shared with The Hacker Information.
“Consequently, we have been capable of create Win-DDoS, a method that may allow an attacker to harness the facility of tens of hundreds of public DCs around the globe to create a malicious botnet with huge sources and add charges. All with out buying something and with out leaving a traceable footprint.”
In reworking DCs right into a DDoS bot with out the necessity for code execution or credentials, the assault basically turns the Home windows platform into changing into each the sufferer and the weapon. The assault circulate is as follows –
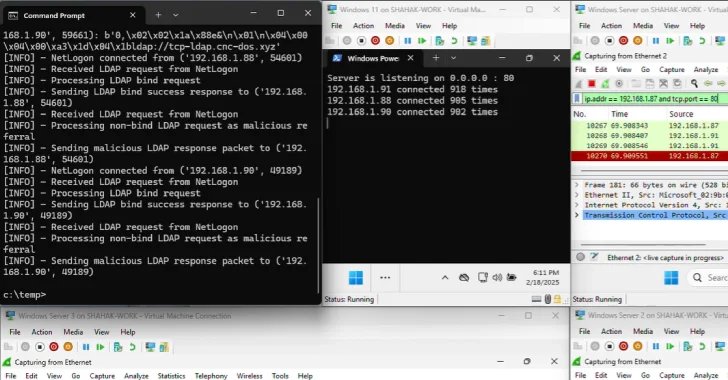
- Attacker sends an RPC name to DCs that triggers them to change into CLDAP shoppers
- DCs ship the CLDAP request to the attacker’s CLDAP server, which then returns a referral response that refers the DCs to the attacker’s LDAP server so as to change from UDP to TCP
- DCs then ship the LDAP question to the attacker’s LDAP server over TCP
- Attacker’s LDAP server responds with an LDAP referral response containing an extended record of LDAP referral URLs, all of which level to a single port on a single IP deal with
- DCs ship an LDAP question on that port, inflicting the online server which may be served through the port to shut the TCP connection

“As soon as the TCP connection is aborted, the DCs proceed to the following referral on the record, which factors to the identical server once more,” the researchers mentioned. “And this habits repeats itself till all of the URLs within the referral record are over, creating our modern Win-DDoS assault approach.”
What makes Win-DDoS important is that it has excessive bandwidth and doesn’t require an attacker to buy devoted infrastructure. Nor does it necessitate them to breach any gadgets, thereby permitting them to fly underneath the radar.
Additional evaluation of the LDAP shopper code referral course of has revealed that it is doable to set off an LSASS crash, reboot, or a blue display of loss of life (BSoD) by sending prolonged referral lists to DCs by benefiting from the truth that there aren’t any limits on referral record sizes and referrals will not be launched from the DC’s heap reminiscence till the data is efficiently retrieved.
On high of that, the transport-agnostic code that is executed to server shopper requests has been discovered to harbor three new denial-of-service (DoS) vulnerabilities that may crash area controllers with out the necessity for authentication, and one further DoS flaw that gives any authenticated person with the flexibility to crash a site controller or Home windows laptop in a site.
The recognized shortcomings are listed beneath –
- CVE-2025-26673 (CVSS rating: 7.5) – Uncontrolled useful resource consumption in Home windows Light-weight Listing Entry Protocol (LDAP) permits an unauthorized attacker to disclaim service over a community (Fastened in Could 2025)
- CVE-2025-32724 (CVSS rating: 7.5) – Uncontrolled useful resource consumption in Home windows Native Safety Authority Subsystem Service (LSASS) permits an unauthorized attacker to disclaim service over a community (Fastened in June 2025)
- CVE-2025-49716 (CVSS rating: 7.5) – Uncontrolled useful resource consumption in Home windows Netlogon permits an unauthorized attacker to disclaim service over a community (Fastened in July 2025)
- CVE-2025-49722 (CVSS rating: 5.7) – Uncontrolled useful resource consumption in Home windows Print Spooler Elements permits a licensed attacker to disclaim service over an adjoining community (Fastened in July 2025)
Just like the LDAPNightmare (CVE-2024-49113) vulnerability detailed earlier this January, the newest findings present that there exist blind spots in Home windows that could possibly be focused and exploited, crippling enterprise operations.
“The vulnerabilities we found are zero-click, unauthenticated vulnerabilities that permit attackers to crash these techniques remotely if they’re publicly accessible, and in addition present how attackers with minimal entry to an inner community can set off the identical outcomes towards personal infrastructure,” the researchers mentioned.
“Our findings break widespread assumptions in enterprise risk modeling: that DoS dangers solely apply to public providers, and that inner techniques are secure from abuse until absolutely compromised. The implications for enterprise resilience, threat modeling, and protection methods are important.”