Cybersecurity researchers are warning of continued dangers posed by a distributed denial-of-service (DDoS) malware often called XorDDoS, with 71.3 p.c of the assaults between November 2023 and February 2025 focusing on america.
“From 2020 to 2023, the XorDDoS trojan has elevated considerably in prevalence,” Cisco Talos researcher Joey Chen stated in a Thursday evaluation.
“This pattern is just not solely as a result of widespread international distribution of the XorDDoS trojan but in addition an uptick in malicious DNS requests linked to its command-and-control (C2) infrastructure. Along with focusing on generally uncovered Linux machines, the trojan has expanded its attain to Docker servers, changing contaminated hosts into bots.”
Practically 42 p.c of the compromised gadgets are situated in america, adopted by Japan, Canada, Denmark, Italy, Morocco, and China.

XorDDoS is a widely known malware that has a monitor report of hanging Linux methods for over a decade. In Could 2022, Microsoft reported a big surge in XorDDoS exercise, with the infections paving the way in which for cryptocurrency mining malware resembling Tsunami.
The first preliminary entry pathway entails conducting Safe Shell (SSH) brute-force assaults to acquire legitimate SSH credentials after which obtain and set up the malware on susceptible IoT and different internet-connected gadgets.
Upon efficiently establishing a foothold, the malware units up persistence utilizing an embedded initialization script and a cron job in order that it launches routinely at system startup. It additionally makes use of the XOR key “BB2FA36AAA9541F0” to decrypt a configuration current inside itself to extract the IP addresses obligatory for C2 communication.
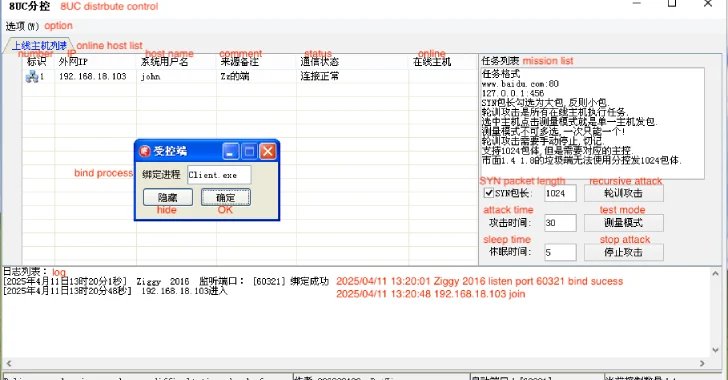
Talos stated it noticed in 2024 a brand new model of the XorDDoS sub-controller, referred to as the VIP model, and its corresponding central controller, together with a builder, indicating that the product is probably going being marketed on the market.
The central controller is chargeable for managing a number of XorDDoS sub-controllers and sending DDoS instructions concurrently. Every of those sub-controllers, in flip, commandeer a botnet of contaminated gadgets.
“The language settings of the multi-layer controller, XorDDoS builder, and controller binding software strongly counsel that the operators are Chinese language-speaking people,” Chen stated.