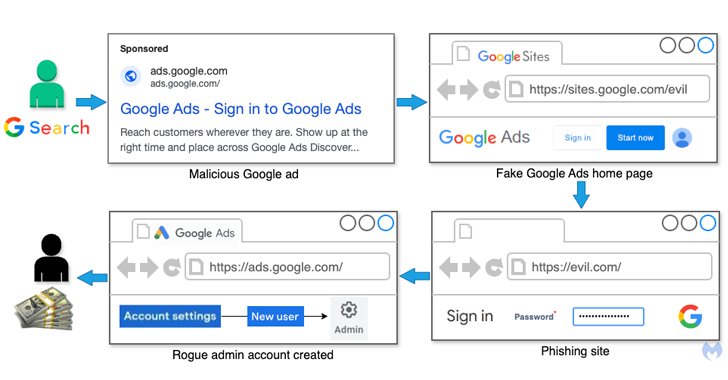
Cybersecurity researchers have alerted to a brand new malvertising marketing campaign that is focusing on people and companies promoting by way of Google Advertisements by trying to phish for his or her credentials by way of fraudulent advertisements on Google.
“The scheme consists of stealing as many advertiser accounts as doable by impersonating Google Advertisements and redirecting victims to pretend login pages,” Jérôme Segura, senior director of menace intelligence at Malwarebytes, stated in a report shared with The Hacker Information.
It is suspected the top objective of the marketing campaign is to reuse the stolen credentials to additional perpetuate the campaigns, whereas additionally promoting them to different prison actors on underground boards. Primarily based on posts shared on Reddit, Bluesky, and Google’s personal help boards, the menace has been energetic since no less than mid-November 2024.
The exercise cluster is quite a bit just like campaigns that leverage stealer malware to steal knowledge associated to Fb promoting and enterprise accounts as a way to hijack them and use the accounts for push-out malvertising campaigns that additional propagate the malware.
The newly recognized marketing campaign particularly singles out customers who seek for Google Advertisements on Google’s personal search engine to serve bogus advertisements for Google Advertisements that, when clicked, redirect customers to fraudulent websites hosted on Google Websites.
These websites then function touchdown pages to steer the guests to exterior phishing websites which might be designed to seize their credentials and two-factor authentication (2FA) codes by way of a WebSocket and exfiltrated to a distant server below the attacker’s management.
“The pretend advertisements for Google Advertisements come from quite a lot of people and companies (together with a regional airport), in varied places,” Segura stated. “A few of these accounts already had tons of of different authentic advertisements working.”

An ingenious facet of the marketing campaign is that it takes benefit of the truth that Google Advertisements doesn’t require the ultimate URL – the online web page that customers attain after they click on on the advert – to be the identical because the show URL, so long as the domains match.
This permits the menace actors to host their intermediate touchdown pages on websites.google[.]com whereas conserving the show URLs as advertisements.google[.]com. What’s extra, the modus operandi entails using methods like fingerprinting, anti-bot site visitors detection, a CAPTCHA-inspired lure, cloaking, and obfuscation to hide the phishing infrastructure.
Malwarebytes stated the harvested credentials are subsequently abused to check in to the sufferer’s Google Advertisements account, add a brand new administrator, and make the most of their spending budgets for pretend Google advertisements.
In different phrases, the menace actors are taking on Google Advertisements accounts to push their very own advertisements as a way to add new victims to a rising pool of hacked accounts which might be used to perpetuate the rip-off additional.
“There seems to be a number of people or teams behind these campaigns,” Segura stated. “Notably, nearly all of them are Portuguese audio system and sure working out of Brazil. The phishing infrastructure depends on middleman domains with the .pt top-level area (TLD), indicative of Portugal.”
“This malicious advert exercise doesn’t violate Google’s advert guidelines. Menace actors are allowed to indicate fraudulent URLs of their advertisements, making them indistinguishable from authentic websites. Google has but to indicate that it takes definitive steps to freeze such accounts till their safety is restored.”
The disclosure comes as Pattern Micro revealed that attackers are utilizing platforms akin to YouTube and SoundCloud to distribute hyperlinks to pretend installers for pirated variations of well-liked software program that in the end result in the deployment of varied malware households akin to Amadey, Lumma Stealer, Mars Stealer, Penguish, PrivateLoader, and Vidar Stealer.
“Menace actors usually use respected file internet hosting providers like Mediafire and Mega.nz to hide the origin of their malware and make detection and elimination tougher,” the corporate stated. “Many malicious downloads are password-protected and encoded, which complicates evaluation in safety environments akin to sandboxes and permits malware to evade early detection.”