Cybersecurity researchers have disclosed particulars of a now-patched privilege escalation vulnerability in Google Cloud Platform (GCP) Cloud Run that might have allowed a malicious actor to entry container pictures and even inject malicious code.
“The vulnerability might have allowed such an id to abuse its Google Cloud Run revision edit permissions with a view to pull personal Google Artifact Registry and Google Container Registry pictures in the identical account,” Tenable safety researcher Liv Matan mentioned in a report shared with The Hacker Information.
The safety shortcoming has been codenamed ImageRunner by the cybersecurity firm. Following accountable disclosure, Google addressed the issue as of January 28, 2025.
Google Cloud Run is a totally managed service for executing containerized purposes in a scalable, serverless surroundings. When the know-how is used to run a service, container pictures are retrieved from the Artifact Registry (or Docker Hub) for subsequent deployment by specifying the picture URL.
At challenge is the truth that there are particular identities that lack container registry permissions however which have edit permissions on Google Cloud Run revisions.
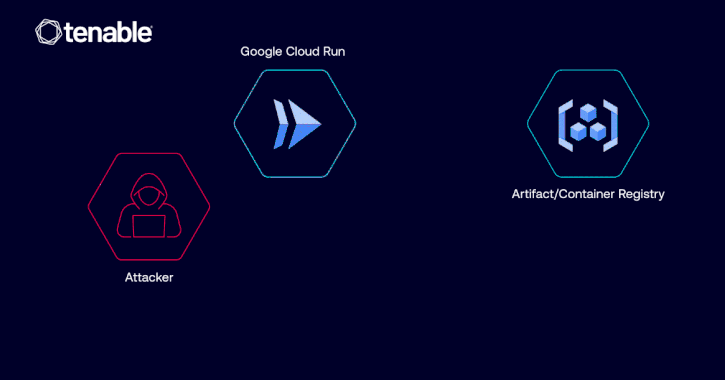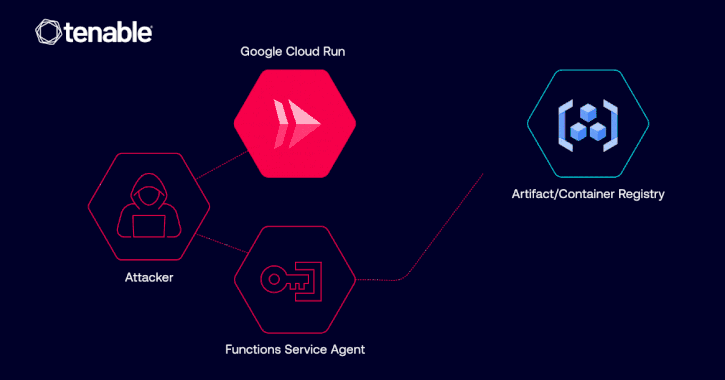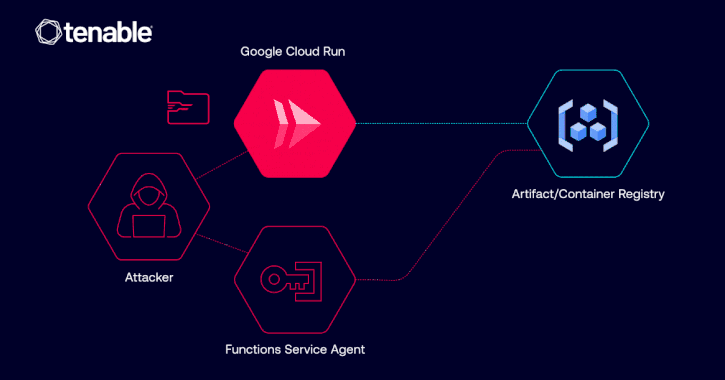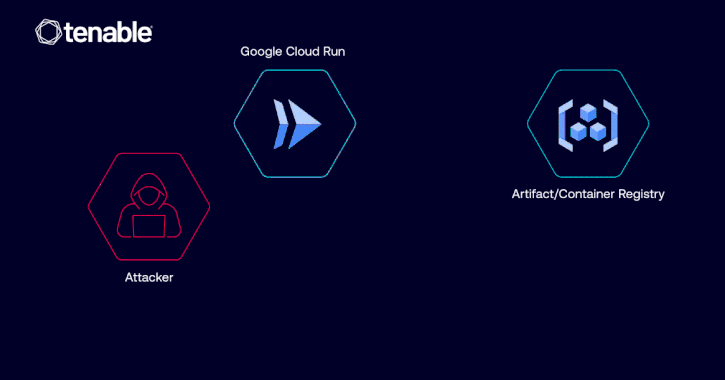
Every time a Cloud Run service is deployed or up to date, a brand new model is created. And every time a Cloud Run revision is deployed, a service agent account is used to drag the required pictures.
“If an attacker beneficial properties sure permissions inside a sufferer’s mission — particularly run.companies.replace and iam.serviceAccounts.actAs permissions — they may modify a Cloud Run service and deploy a brand new revision,” Matan defined. “In doing so, they may specify any personal container picture throughout the similar mission for the service to drag.”
What’s extra, the attacker might entry delicate or proprietary pictures saved in a sufferer’s registries and even introduce malicious directions that, when executed, could possibly be abused to extract secrets and techniques, exfiltrate delicate information, and even open a reverse shell to a machine below their management.
The patch launched by Google now ensures that the person or service account creating or updating a Cloud Run useful resource has specific permission to entry the container pictures.
“The principal (person or service account) creating or updating a Cloud Run useful resource now wants specific permission to entry the container picture(s),” the tech big mentioned in its launch notes for Cloud Run in January 2025.
“When utilizing Artifact Registry, make sure the principal has the Artifact Registry Reader (roles/artifactregistry.reader) IAM function on the mission or repository containing the container picture(s) to deploy.”
Tenable has characterised ImageRunner for instance of what it calls Jenga, which arises as a result of interconnected nature of varied cloud companies, inflicting safety dangers to be handed alongside.
“Cloud suppliers construct their companies on high of their different current companies,” Matan mentioned. “If one service will get attacked or is compromised, the opposite ones constructed on high of it inherit the danger and turn into susceptible as nicely.”
“This situation opens the door for attackers to find novel privilege escalation alternatives and even vulnerabilities, and introduces new hidden dangers for defenders.”
The disclosure comes weeks after Praetorian detailed a number of methods a lower-privilege principal can abuse an Azure digital machine (VM) to realize management over an Azure subscription –
- Execute instructions on an Azure VM related to an administrative managed id
- Log in to an Azure VM related to an administrative managed id
- Connect an current administrative user-assigned managed id to an current Azure VM and execute instructions in that VM
- Create a brand new Azure VM, connect an current administrative managed id to it, and execute instructions in that VM through the use of information aircraft actions
“After acquiring the Proprietor function for a subscription, an attacker might be able to leverage their broad management over all subscription assets to discover a privilege escalation path to the Entra ID tenant,” safety researchers Andrew Chang and Elgin Lee mentioned.
“This path is based on a compute useful resource within the sufferer subscription with a service principal with Entra ID permissions that will permit it to escalate itself to International Administrator.”