A cross-site scripting (XSS) vulnerability in a digital tour framework has been weaponized by malicious actors to inject malicious scripts throughout lots of of internet sites with the purpose of manipulating search outcomes and fueling a spam adverts marketing campaign at scale.
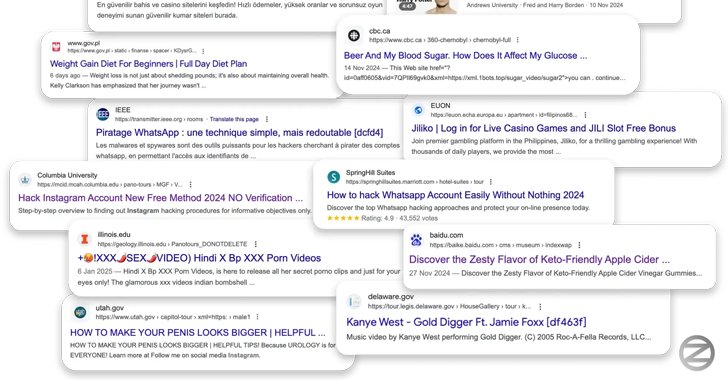
Safety researcher Oleg Zaytsev, in a report shared with The Hacker Information, stated the marketing campaign – dubbed 360XSS – affected over 350 web sites, together with authorities portals, U.S. state authorities websites, American universities, main resort chains, information shops, automotive dealerships, and a number of other Fortune 500 firms.
“This wasn’t only a spam operation,” the researcher stated. “It was an industrial-scale abuse of trusted domains.”
All these web sites have one factor in frequent: A preferred framework known as Krpano that is used to embed 360° pictures and movies to facilitate interactive digital excursions and VR experiences.
Zaytsev stated he stumbled upon the marketing campaign after coming throughout a pornography-related advert listed on Google Search however with a website related to Yale College (“virtualtour.quantuminstitute.yale[.]edu”).
A notable facet of those URLs is an XML parameter that is designed to redirect the positioning customer to a second URL that belongs to a different professional web site, which is then used to execute a Base64-encoded payload by way of an XML doc. The decoded payload, for its half, fetches the goal URL (i.e., the advert) from yet one more professional web site.
The XML parameter handed within the authentic URL served within the search outcomes is a part of a broader configuration setting named “passQueryParameters” that is used when embedding a Krpano panorama viewer into an HTML web page. It is particularly designed to cross HTTP parameters from the URL to the viewer.
The safety challenge right here is that if the choice is enabled, it opens the door to a situation the place an attacker may use a specifically crafted URL to execute a malicious script in a sufferer’s net browser when the susceptible web site is visited.
Certainly, a mirrored XSS flaw arising on account of this habits was disclosed in Krpano in late 2020 (CVE-2020-24901, CVSS rating: 6.1), indicating that the potential for abuse has been publicly recognized for over 4 years.
Whereas an replace launched in model 1.20.10 restricted “passQueryParameters” to an allowlist in an try to stop such XSS assaults from happening, Zaytsev discovered that explicitly including the XML parameter to the allowlist reintroduced the XSS danger.

“Since model 1.20.10, Krpano’s default set up was not susceptible,” the researcher advised The Hacker Information by way of e mail. “Nonetheless, configuring passQueryParameter together with the XML parameter allowed exterior XML configuration by way of the URL, resulting in an XSS danger.”
“The exploited variations I’ve come throughout had been primarily older ones, predating model 1.20.10.”
The marketing campaign, per Zaytsev, has leveraged this weak point to hijack over 350 websites to serve sketchy adverts associated to pornography, food regimen dietary supplements, on-line casinos, and pretend information websites. What’s extra, a few of these pages have been weaponized to spice up YouTube video views.
The marketing campaign is noteworthy, not least as a result of it abuses the belief and credibility of professional domains to indicate up prominently in search outcomes, a way known as search engine marketing (search engine marketing) poisoning, which, in flip, is completed by abusing the XSS flaw.
“A mirrored XSS is a enjoyable vulnerability however by itself requires consumer interplay, and one of many largest challenges is to make folks click on your mirrored XSS hyperlink,” Zaytsev stated. “So utilizing engines like google as a distribution platform to your XSS is a really artistic and funky strategy to do it.”
Following accountable disclosure, the most recent launch of Krpano eliminates help for exterior configuration by way of the XML parameter, thereby mitigating the chance of XSS assaults even when the setting is used.
“Improved embedpano() passQueryParameters safety: data-urls and exterior URLs are usually not allowed as parameter values anymore and URLs for the XML parameter are restricted to be throughout the present folder construction,” in accordance with the discharge notes for model 1.22.4 launched this week.
It is at present not recognized who’s behind the large operation, though the abuse of an XSS flaw to serve simply redirects, versus finishing up extra nefarious assaults like credential or cookie theft, raises the potential of an advert agency with questionable practices that is serving these adverts as a monetization technique.
Customers of Krpano are suggested to replace their installations to the most recent model and set the “passQueryParameters” setting to false. Affected web site homeowners are beneficial to seek out and take away contaminated pages by way of Google Search Console.