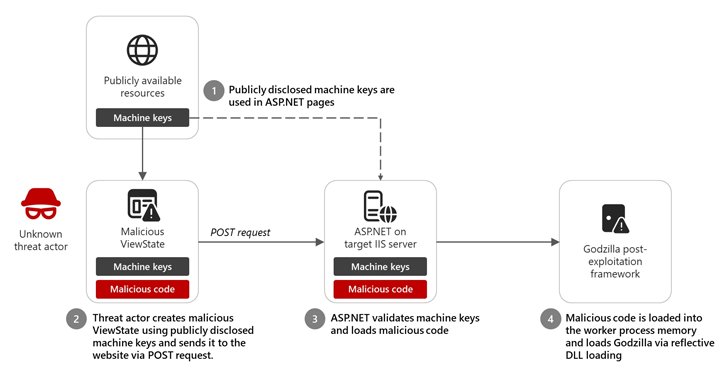
Microsoft is warning of an insecure apply whereby software program builders are incorporating publicly disclosed ASP.NET machine keys from publicly accessible assets, thereby placing their functions in attackers’ pathway.
The tech big’s menace intelligence workforce stated it noticed restricted exercise in December 2024 that concerned an unknown menace actor utilizing a publicly accessible, static ASP.NET machine key to inject malicious code and ship the Godzilla post-exploitation framework.
It additionally famous that it has recognized over 3,000 publicly disclosed keys that could possibly be used for a majority of these assaults, which it is calling ViewState code injection assaults.
“Whereas many beforehand identified ViewState code injection assaults used compromised or stolen keys which are usually bought on darkish internet boards, these publicly disclosed keys may pose a better threat as a result of they’re accessible in a number of code repositories and will have been pushed into improvement code with out modification,” Microsoft stated.
ViewState is a technique used within the ASP.NET framework to protect web page and management values between postbacks. This could additionally embrace software information that’s particular to a web page.
“By default, view state information is saved within the web page in a hidden subject and is encoded utilizing base64 encoding,” Microsoft notes in its documentation. “As well as, a hash of the view state information is created from the information by utilizing a machine authentication code (MAC) key. The hash worth is added to the encoded view state information and the ensuing string is saved within the web page.”
In utilizing a hash worth, the thought is to make sure that the view state information has not been corrupted or tampered with by malicious actors. That stated, if these keys are stolen or made accessible to unauthorized third-parties, it opens the door to a situation the place the menace actor can leverage the keys to ship a malicious ViewState request and execute arbitrary code.
“When the request is processed by ASP.NET Runtime on the focused server, the ViewState is decrypted and validated efficiently as a result of the appropriate keys are used,” Redmond famous. “The malicious code is then loaded into the employee course of reminiscence and executed, offering the menace actor distant code execution capabilities on the goal IIS internet server.”
Microsoft has supplied a listing of hash values for the publicly disclosed machine keys, urging prospects to examine them towards the machine keys used of their environments. It has additionally warned that within the occasion of a profitable exploitation of publicly disclosed keys, merely rotating the keys is not going to be ample because the menace actors could have already established persistence on the host.
To mitigate the chance posed by such assaults, it is suggested to not copy keys from publicly accessible sources and to frequently rotate keys. As an extra step to discourage menace actors, Microsoft stated it eliminated key artifacts from “restricted situations” the place they had been included in its documentation.
The event comes as cloud safety firm Aqua revealed particulars of an OPA Gatekeeper bypass that could possibly be exploited to conduct unauthorized actions in Kubernetes environments, together with deploying unauthorized container photos.
“Within the k8sallowedrepos coverage, a safety threat arises from how the Rego logic is written within the ConstraintTemplate file,” researchers Yakir Kadkoda and Assaf Morag stated in an evaluation shared with The Hacker Information.
“This threat is additional amplified when customers outline values within the Constraint YAML file that don’t align with how the Rego logic processes them. This mismatch can lead to coverage bypasses, making the restrictions ineffective.”