Cybersecurity researchers have uncovered three safety weaknesses in Microsoft’s Azure Knowledge Manufacturing facility Apache Airflow integration that, if efficiently exploited, may have allowed an attacker to realize the power to conduct varied covert actions, together with information exfiltration and malware deployment.
“Exploiting these flaws may permit attackers to realize persistent entry as shadow directors over the complete Airflow Azure Kubernetes Service (AKS) cluster,” Palo Alto Networks Unit 42 mentioned in an evaluation revealed earlier this month.
The vulnerabilities, albeit categorized as low severity by Microsoft, are listed beneath –
- Misconfigured Kubernetes RBAC in Airflow cluster
- Misconfigured secret dealing with of Azure’s inner Geneva service, and
- Weak authentication for Geneva
In addition to acquiring unauthorized entry, the attacker may make the most of the failings within the Geneva service to doubtlessly tamper with log information or ship pretend logs to keep away from elevating suspicion when creating new pods or accounts.
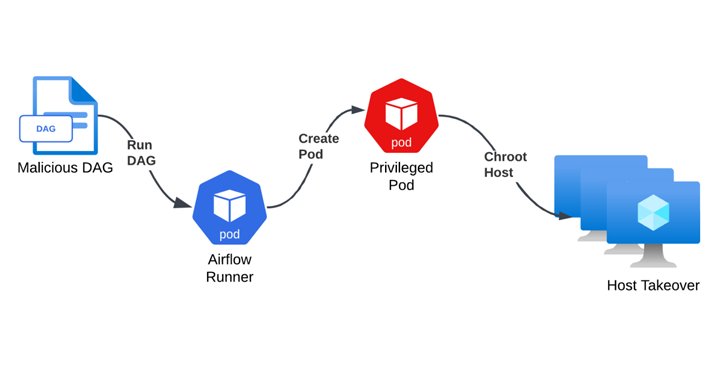
The preliminary entry method entails crafting a directed acyclic graph (DAG) file and importing it to a non-public GitHub repository linked to the Airflow cluster, or altering an current DAG file. The top purpose is to launch a reverse shell to an exterior server as quickly because it’s imported.
To drag this off, the menace actor must first acquire write permissions to the storage account containing DAG recordsdata by using a compromised service principal or a shared entry signature (SAS) token for the recordsdata. Alternatively, they will break right into a Git repository utilizing leaked credentials.
Though the shell obtained on this method was discovered to be working below the context of the Airflow consumer in a Kubernetes pod with minimal permissions, additional evaluation recognized a service account with cluster-admin permissions linked to the Airflow runner pod.
This misconfiguration, coupled with the truth that the pod might be reachable over the web, meant that the attacker may obtain the Kubernetes command-line software kubectl and finally take full management of the complete cluster by “deploying a privileged pod and breaking out onto the underlying node.”

The attacker may then leverage the foundation entry to the host digital machine (VM) to burrow deeper into the cloud surroundings, acquire unauthorized entry to Azure-managed inner assets, together with Geneva, a few of which grant write entry to storage accounts and occasion hubs.
“This implies a complicated attacker may modify a susceptible Airflow surroundings,” safety researchers Ofir Balassiano and David Orlovsky mentioned. “For instance, an attacker may create new pods and new service accounts. They might additionally apply adjustments to the cluster nodes themselves after which ship pretend logs to Geneva with out elevating an alarm.”
“This challenge highlights the significance of fastidiously managing service permissions to stop unauthorized entry. It additionally highlights the significance of monitoring the operations of important third-party providers to stop such entry.”
The disclosure comes because the Datadog Safety Labs detailed a privilege escalation situation in Azure Key Vault that might allow customers with the Key Vault Contributor function to learn or modify Key Vault contents, corresponding to API keys, passwords, authentication certificates, and Azure Storage SAS tokens.
The issue is that whereas a consumer with the Key Vault Contributor function had no direct entry to Key Vault information over a key vault configured with entry insurance policies, it was found that the function did include permissions so as to add itself to Key Vault entry insurance policies and entry Key Vault information, successfully bypassing the restriction.
“A coverage replace may include the power to checklist, view, replace and customarily handle the info inside the important thing vault,” safety researcher Katie Knowles mentioned. “This created a situation the place a consumer with the Key Vault Contributor function may acquire entry to all Key Vault information, regardless of having no [Role-Based Access Control] permission to handle permissions or view information.”
Microsoft has since up to date its documentation to emphasise the entry coverage danger, stating: “To forestall unauthorized entry and administration of your key vaults, keys, secrets and techniques, and certificates, it is important to restrict Contributor function entry to key vaults below the Entry Coverage permission mannequin.”
The event additionally follows the invention of a problem with Amazon Bedrock CloudTrail logging that made it tough to distinguish malicious queries from professional ones made to massive language fashions (LLMs), thereby permitting unhealthy actors to conduct reconnaissance with out elevating any alert.
“Particularly, failed Bedrock API calls have been logged in the identical method as profitable calls, with out offering any particular error codes,” Sysdig researcher Alessandro Brucato mentioned.
“The shortage of error info in API responses might hinder detection efforts by producing false positives in CloudTrail logs. With out this element, safety instruments might misread regular exercise as suspicious, resulting in pointless alerts and potential oversight of real threats.”