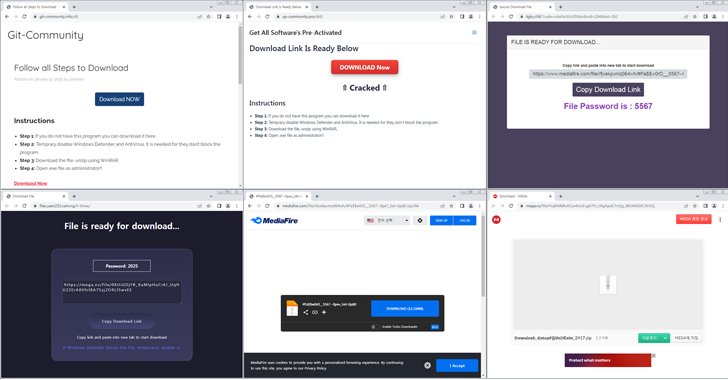
Cybersecurity researchers are warning of a brand new marketing campaign that leverages cracked variations of software program as a lure to distribute info stealers like Lumma and ACR Stealer.
The AhnLab Safety Intelligence Middle (ASEC) stated it has noticed a spike within the distribution quantity of ACR Stealer since January 2025.
A notable side of the stealer malware is using a method referred to as lifeless drop resolver to extract the precise command-and-control (C2) server. This contains counting on authentic companies like Steam, Telegram’s Telegraph, Google Types, and Google Slides.
“Risk actors enter the precise C2 area in Base64 encoding on a particular web page,” ASEC stated. “The malware accesses this web page, parses the string, and obtains the precise C2 area deal with to carry out malicious behaviors.”
ACR Stealer, beforehand distributed by way of Hijack Loader malware, is able to harvesting a variety of data from compromised methods, together with information, net browser information, and cryptocurrency pockets extensions.
The event comes as ASEC revealed one other marketing campaign that makes use of information with the extension “MSC,” which will be executed by the Microsoft Administration Console (MMC), to ship the Rhadamanthys stealer malware.
“There are two sorts of MSC malware: one exploits the vulnerability of apds.dll (CVE-2024-43572), and the opposite executes the ‘command’ command utilizing Console Taskpad,” the South Korean firm stated.
“The MSC file is disguised as an MS Phrase doc. “When the ‘Open’ button is clicked, it downloads and executes a PowerShell script from an exterior supply. The downloaded PowerShell script accommodates an EXE file (Rhadamanthys).”
CVE-2024-43572, additionally referred to as GrimResource, was first documented by the Elastic Safety Labs in June 2024 as having been exploited by malicious actors as a zero-day. It was patched by Microsoft in October 2024.
Malware campaigns have additionally been noticed exploiting chat assist platforms like Zendesk, masquerading as clients to trick unsuspecting assist brokers into downloading a stealer referred to as Zhong Stealer.
In response to a current report printed by Hudson Rock, over 30,000,000 computer systems have been contaminated by info stealers within the “previous few years,” resulting in the theft of company credentials and session cookies that would then be offered by cybercriminals on underground boards to different actors for revenue.
The consumers may weaponize the entry afforded by these credentials to stage post-exploitation actions of their very own, resulting in extreme dangers. These developments serve to spotlight the function performed by stealer malware as an preliminary entry vector that gives a foothold to delicate company environments.
“For as little as $10 per log (laptop), cybercriminals should purchase stolen information from staff working in categorised protection and army sectors,” Hudson Rock stated. “Infostealer intelligence is not nearly detecting who’s contaminated — it is about understanding the total community of compromised credentials and third-party dangers.”
Over the previous yr, menace actors have additionally been ramping up efforts to unfold quite a lot of malware households, together with stealers and distant entry trojans (RATs), by way of a method referred to as ClickFix that usually entails redirecting customers to pretend CAPTCHA verification pages instructing them to repeat and execute nefarious PowerShell instructions.
One such payload dropped is I2PRAT, which employs the I2P anonymization community to anonymize its closing C2 server.
“The malware is a sophisticated menace composed of a number of layers, every incorporating subtle mechanisms,” Sekoia stated. “The usage of an anonymization community complicates monitoring and hinders the identification of the menace’s magnitude and unfold within the wild.”