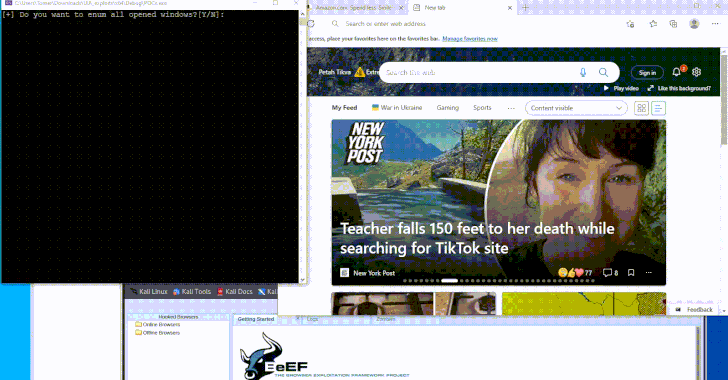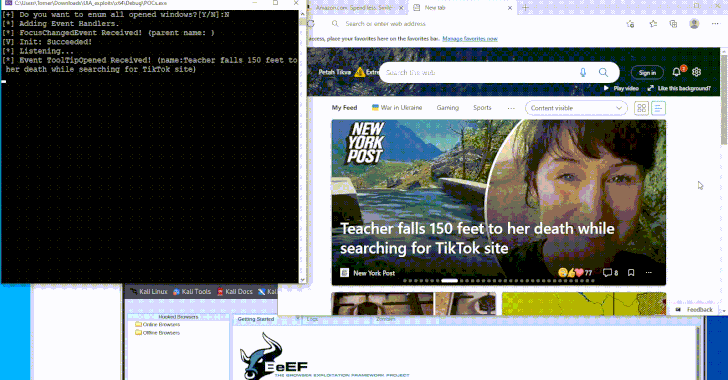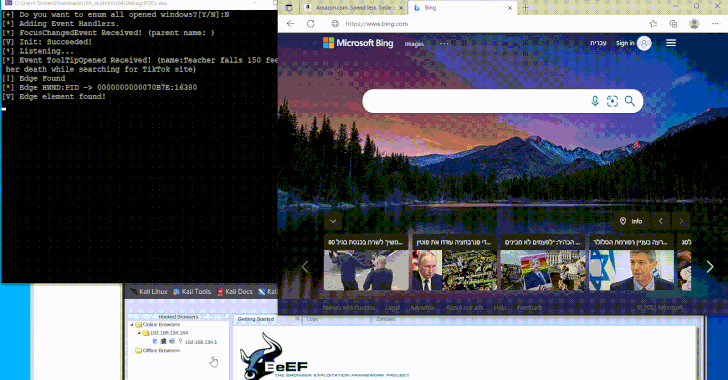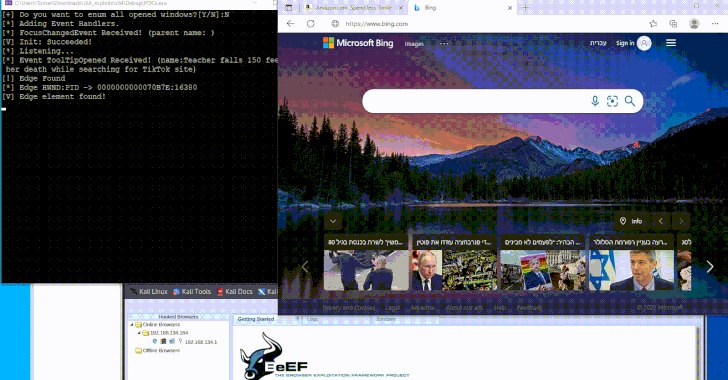
A newly devised method leverages a Home windows accessibility framework known as UI Automation (UIA) to carry out a variety of malicious actions with out tipping off endpoint detection and response (EDR) options.
“To use this system, a person have to be satisfied to run a program that makes use of UI Automation,” Akamai safety researcher Tomer Peled mentioned in a report shared with The Hacker Information. “This will result in stealthy command execution, which might harvest delicate information, redirect browsers to phishing web sites, and extra.”
Even worse, native attackers might benefit from this safety blindspot to execute instructions and browse/write messages from/to messaging purposes like Slack and WhatsApp. On prime of that, it is also doubtlessly weaponized to govern UI components over a community.
First obtainable in Home windows XP as a part of the Microsoft .NET Framework, UI Automation is designed to offer programmatic entry to numerous person interface (UI) components and assist customers manipulate them utilizing assistive know-how merchandise, resembling display readers. It can be utilized in automated testing situations.
“Assistive know-how purposes usually want entry to the protected system UI components, or to different processes that is likely to be operating at a better privilege stage,” Microsoft notes in a help doc. “Subsequently, assistive know-how purposes have to be trusted by the system, and should run with particular privileges.”
“To get entry to larger IL processes, an assistive know-how utility should set the UIAccess flag within the utility’s manifest and be launched by a person with administrator privileges.”
The UI interactions with components in different purposes are achieved by making use of the Part Object Mannequin (COM) as an inter-process communication (IPC) mechanism. This makes it attainable to create UIA objects that can be utilized to work together with an utility that is in focus by organising an occasion handler that is triggered when sure UI modifications are detected.

Akamai’s analysis discovered that this strategy might additionally open up an avenue for abuse, permitting malicious actors to learn/write messages, steal information entered in web sites (e.g., cost data), and execute instructions that redirect victims to malicious web sites when a at the moment displayed net web page in a browser refreshes or modifications.
“Along with the UI components at the moment proven on the display that we will work together with, extra components are loaded prematurely and positioned in a cache,” Peled famous. “We are able to additionally work together with these components, resembling studying messages not proven on the display, and even set the textual content field and ship messages with out it being mirrored on the display.”
That mentioned, it bears noting that every of those malicious situations is an meant function of UI Automation, similar to how Android’s accessibility companies API has change into a staple means for malware to extract data from compromised gadgets.
“This goes again to the meant function of the appliance: These permissions ranges should exist as a way to use it,” Peled added. “That is why UIA is ready to bypass Defender — the appliance finds nothing out of the atypical. If one thing is seen as a function reasonably than a bug, the machine’s logic will observe the function.”
From COM to DCOM: A Lateral Motion Assault Vector
The disclosure comes as Deep Intuition revealed that the Distributed COM (DCOM) distant protocol, which permits software program parts to speak over a community, may very well be exploited to remotely write customized payloads to create an embedded backdoor.
The assault “permits the writing of customized DLLs to a goal machine, loading them to a service, and executing their performance with arbitrary parameters,” safety researcher Eliran Nissan mentioned. “This backdoor-like assault abuses the IMsiServer COM interface.”
That mentioned, the Israeli cybersecurity firm famous that an assault of this sort leaves clear indicators of compromise (IoCs) that may be detected and blocked. It additional requires the attacker and sufferer machines to be in the identical area.

“Till now, DCOM lateral motion assaults have been completely researched on IDispatch-based COM objects attributable to their scriptable nature,” Nissan mentioned. The brand new ‘DCOM Add & Execute’ methodology “remotely writes customized payloads to the sufferer’s [Global Assembly Cache], executes them from a service context, and communicates with them, successfully functioning as an embedded backdoor.”
“The analysis introduced right here proves that many surprising DCOM objects could also be exploitable for lateral motion, and correct defenses must be aligned.”