Cybersecurity researchers have make clear a beforehand undocumented risk actor known as NightEagle (aka APT-Q-95) that has been noticed focusing on Microsoft Change servers as part of a zero-day exploit chain designed to focus on authorities, protection, and expertise sectors in China.
In line with QiAnXin’s RedDrip Group, the risk actor has been energetic since 2023 and has switched community infrastructure at an especially quick fee. The findings have been offered at CYDES 2025, the third version of Malaysia’s Nationwide Cyber Defence & Safety Exhibition and Convention held between July 1 and three, 2025.
“It appears to have the velocity of an eagle and has been working at evening in China,” the cybersecurity vendor stated, explaining the rationale behind naming the adversary NightEagle.
Assaults mounted by the risk actor have singled out entities working within the high-tech, chip semiconductors, quantum expertise, synthetic intelligence, and navy verticals with the primary purpose of gathering intelligence, QiAnXin added.
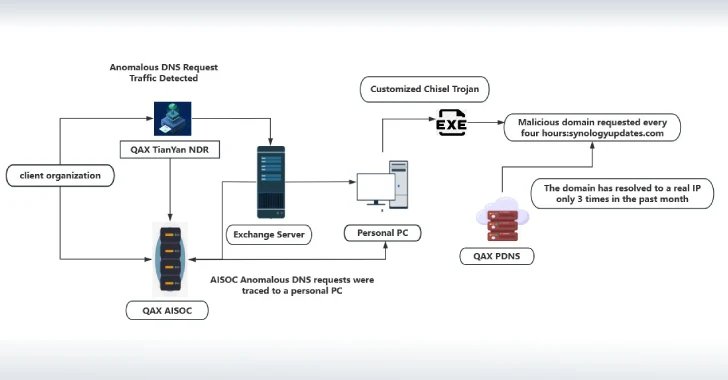
The corporate additionally famous that it started an investigation after it found a bespoke model of the Go-based Chisel utility on one in all its buyer’s endpoints which was configured to robotically begin each 4 hours as a part of a scheduled job.

“The attacker modified the supply code of the open-source Chisel intranet penetration instrument, hard-coded the execution parameters, used the required username and password, established a socks reference to the 443 finish of the required C&C handle, and mapped it to the required port of the C&C host to attain the intranet penetration perform,” it stated in a report.
It is stated that the trojan is delivered by the use of a .NET loader, which, in flip, is implanted into the Web Info Server (IIS) service of the Microsoft Change Server. Additional evaluation has decided the presence of a zero-day that enabled the attackers to acquire the machineKey and acquire unauthorized entry to the Change Server.
“The attacker used the important thing to deserialize the Change server, thereby implanting a Trojan into any server that complies with the Change model, and remotely studying the mailbox knowledge of any individual,” the report stated.
QiAnXin claimed that the exercise was probably the work of a risk actor from North America on condition that the assaults passed off between 9 p.m. and 6 a.m. Beijing time. The Hacker Information has reached out to Microsoft for additional remark, and we’ll replace the story if we get a response.