Uncovered PostgreSQL situations are the goal of an ongoing marketing campaign designed to achieve unauthorized entry and deploy cryptocurrency miners.
Cloud safety agency Wiz mentioned the exercise is a variant of an intrusion set that was first flagged by Aqua Safety in August 2024 that concerned using a malware pressure dubbed PG_MEM. The marketing campaign has been attributed to a risk actor Wiz tracks as JINX-0126.
“The risk actor has since developed, implementing protection evasion methods reminiscent of deploying binaries with a novel hash per goal and executing the miner payload filelessly – more likely to evade detection by [cloud workload protection platform] options that rely solely on file hash popularity,” researchers Avigayil Mechtinger, Yaara Shriki, and Gili Tikochinski mentioned.
Wiz has additionally revealed that the marketing campaign has possible claimed over 1,500 victims to this point, indicating that publicly-exposed PostgreSQL situations with weak or predictable credentials are prevalent sufficient to turn out to be an assault goal for opportunistic risk actors.
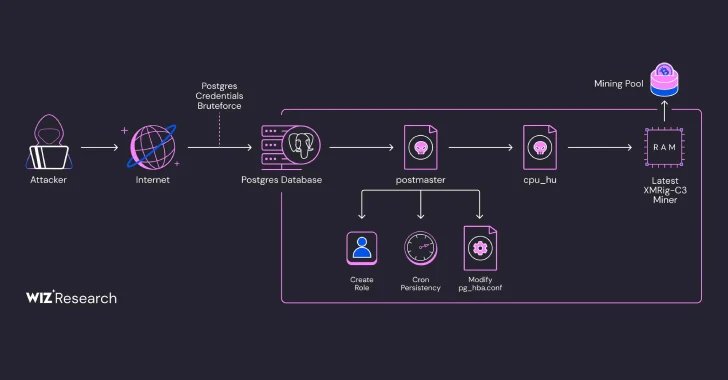
Probably the most distinctive facet of the marketing campaign is the abuse of the COPY … FROM PROGRAM SQL command to execute arbitrary shell instructions on the host.

The entry afforded by the profitable exploitation of weakly configured PostgreSQL companies is used to conduct preliminary reconnaissance and drop a Base64-encoded payload, which, in actuality, is a shell script that kills competing cryptocurrency miners and drops a binary named PG_CORE.
Additionally downloaded to the server is an obfuscated Golang binary codenamed postmaster that mimics the professional PostgreSQL multi-user database server. It is designed to arrange persistence on the host utilizing a cron job, create a brand new position with elevated privileges, and write one other binary referred to as cpu_hu to disk.
cpu_hu, for its half, downloads the newest model of the XMRig miner from GitHub and launches it filelessly by way of a recognized Linux fileless approach known as memfd.
“The risk actor is assigning a novel mining employee to every sufferer,” Wiz mentioned, including it recognized three completely different wallets linked to the risk actor. “Every pockets had roughly 550 staff. Mixed, this means that the marketing campaign may have leveraged over 1,500 compromised machines.”