Russian organizations have grow to be the goal of a phishing marketing campaign that distributes malware referred to as PureRAT, in response to new findings from Kaspersky.
“The marketing campaign aimed toward Russian enterprise started again in March 2023, however within the first third of 2025 the variety of assaults quadrupled in comparison with the identical interval in 2024,” the cybersecurity vendor mentioned.
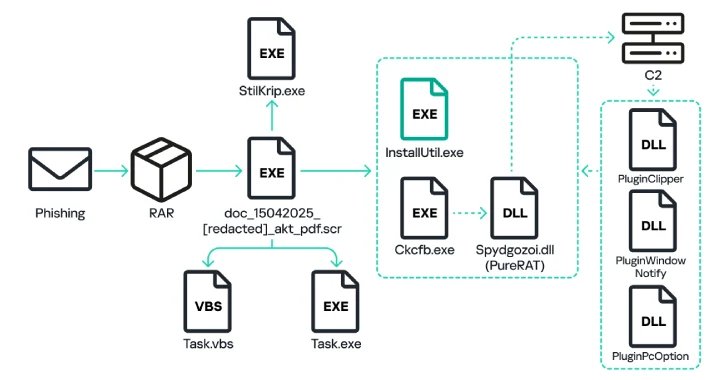
The assault chains, which haven’t been attributed to any particular risk actor, begin with a phishing electronic mail that incorporates a RAR file attachment or a hyperlink to the archive that masquerades as a Microsoft Phrase or a PDF doc by making use of double extensions (“doc_054_[redacted].pdf.rar”).
Current throughout the archive file is an executable that, when launched, copies itself to the “%AppData%” location of the compromised Home windows machine below the identify “activity.exe” and creates a Visible Primary Script referred to as “Job.vbs” within the Startup VBS folder.
The executable then proceeds to unpack one other executable “ckcfb.exe”, runs the system utility “InstallUtil.exe,” and injects into it the decrypted module. “Ckcfb.exe,” for its half, extracts and decrypts a DLL file “Spydgozoi.dll” that comes with the primary payload of the PureRAT malware.
PureRAT establishes SSL connections with a command-and-control (C2) server and transmits system data, together with particulars concerning the antivirus merchandise put in, the pc identify, and the time elapsed because the system startup. In response, the C2 server sends auxiliary modules to carry out quite a lot of malicious actions –
- PluginPcOption, which is able to executing instructions for self-deletion, restarting the executable file, and shutting down or rebooting the pc
- PluginWindowNotify, which checks the identify of the lively window for key phrases like password, financial institution, WhatsApp, and carry out acceptable follow-up actions like unauthorized fund transfers
- PluginClipper, which features as a clipper malware by substituting cryptocurrency pockets addresses copied to the system’s clipboard with an attacker-controlled one
“The Trojan contains modules for downloading and working arbitrary recordsdata that present full entry to the file system, registry, processes, digital camera and microphone, implement keylogger performance, and provides attackers the flexibility to secretly management the pc utilizing the distant desktop precept,” Kaspersky mentioned.

The unique executable that launches “ckcfb.exe” concurrently additionally extracts a second binary known as “StilKrip.exe,” which is a commercially obtainable downloader dubbed PureCrypter that has been used to ship numerous payloads up to now. It is lively since 2022.
“StilKrip.exe” is designed to obtain “Bghwwhmlr.wav,” which follows the aforementioned assault sequence to run “InstallUtil.exe” and finally launch “Ttcxxewxtly.exe,” an executable that unpacks and runs a DLL payload referred to as PureLogs (“Bftvbho.dll”).
PureLogs is an off-the-shelf data stealer that may harvest knowledge from internet browsers, electronic mail purchasers, VPN companies, messaging apps, pockets browser extensions, password managers, cryptocurrency pockets apps, and different applications like FileZilla and WinSCP.
“The PureRAT backdoor and PureLogs stealer have broad performance that permits attackers to realize limitless entry to contaminated methods and confidential group knowledge,” Kaspersky mentioned. “The principle vector of assaults on companies has been and stays emails with malicious attachments or hyperlinks.”