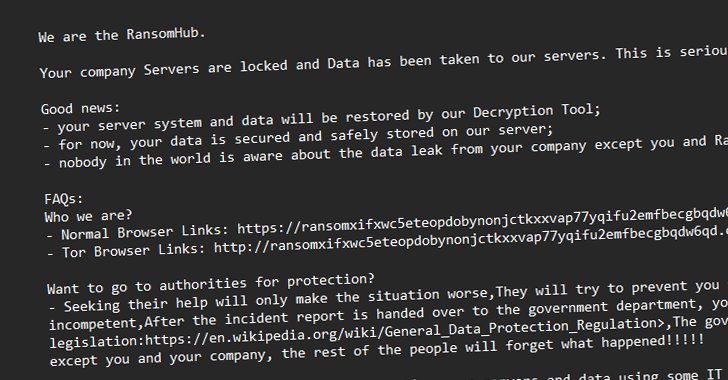
The risk actors behind the RansomHub ransomware-as-a-service (RaaS) scheme have been noticed leveraging now-patched safety flaws in Microsoft Energetic Listing and the Netlogon protocol to escalate privileges and acquire unauthorized entry to a sufferer community’s area controller as a part of their post-compromise technique.
“RansomHub has focused over 600 organizations globally, spanning sectors akin to healthcare, finance, authorities, and important infrastructure, firmly establishing it as essentially the most energetic ransomware group in 2024,” Group-IB analysts stated in an exhaustive report printed this week.
The ransomware group first emerged in February 2024, buying the supply code related to the now-defunct Knight (previously Cyclops) RaaS gang from the RAMP cybercrime discussion board to hurry up its operations. About 5 months later, an up to date model of the locker was marketed on the illicit market with capabilities to remotely encrypt information by way of SFTP protocol.
It is available in a number of variants which can be able to encrypting information on Home windows, VMware ESXi, and SFTP servers. RansomHub has additionally been noticed actively recruiting associates from LockBit and BlackCat teams as a part of a partnership program, indicating an try and capitalize on the legislation enforcement actions concentrating on its rivals.
Within the incident analyzed by the Singaporean cybersecurity firm, the risk actor is claimed to have unsuccessfully tried to take advantage of a important flaw impacting Palo Alto Networks PAN-OS units (CVE-2024-3400) utilizing a publicly obtainable proof-of-concept (PoC), earlier than finally breaching the sufferer community by the use of a brute-force assault in opposition to the VPN service.
“This brute pressure try was primarily based on an enriched dictionary of over 5,000 usernames and passwords,” the researchers stated. “The attacker ultimately gained entry via a default account regularly utilized in information backup options, and the perimeter was lastly breached.”
The preliminary entry was then abused to hold out the ransomware assault, with each information encryption and exfiltration occurring inside 24 hours of the compromise.
Significantly, it concerned the weaponization of two recognized safety flaws in Energetic Listing (CVE-2021-42278 aka noPac) and the Netlogon protocol (CVE-2020-1472 aka ZeroLogon) to grab management of the area controller and conduct lateral motion throughout the community.

“The exploitation of the above-mentioned vulnerabilities enabled the attacker to realize full privileged entry to the area controller, which is the nerve middle of a Microsoft Home windows-based infrastructure,” the researchers stated.
“Following the completion of the exfiltration operations, the attacker ready the surroundings for the ultimate section of the assault. The attacker operated to render all firm information, saved on the assorted NAS, utterly unreadable and inaccessible, in addition to impermissible to revive, with the goal of forcing the sufferer to pay the ransom to get their information again.”
One other notable side of the assault is the usage of PCHunter to cease and bypass endpoint safety options, in addition to Filezilla for information exfiltration.
“The origins of the RansomHub group, its offensive operations, and its overlapping traits with different teams affirm the existence of a vivid cybercrime ecosystem,” the researchers stated.
“This surroundings thrives on the sharing, reusing, and rebranding of instruments and supply codes, fueling a sturdy underground market the place high-profile victims, notorious teams, and substantial sums of cash play central roles.”
The event comes because the cybersecurity agency detailed the internal workings of a “formidable RaaS operator” generally known as Lynx, shedding gentle on their affiliate workflow, their cross-platform ransomware arsenal for Home windows, Linux, and ESXi environments, and customizable encryption modes.
An evaluation of the ransomware’s Home windows and Linux variations exhibits that it intently resembles INC ransomware, indicating that the risk actors seemingly acquired the latter’s supply code.
“Associates are incentivized with an 80% share of ransom proceeds, reflecting a aggressive, recruitment-driven technique,” it stated. “Lynx just lately added a number of encryption modes: ‘quick,’ ‘medium,’ ‘gradual,’ and ‘whole,’ giving associates the liberty to regulate the trade-off between velocity and depth of file encryption.”
“The group’s recruitment posts on underground boards emphasize a stringent verification course of for pentesters and expert intrusion groups, highlighting Lynx’s emphasis on operational safety and high quality management. Additionally they provide ‘name facilities’ for harassing victims and superior storage options for associates who constantly ship worthwhile outcomes.”

In current weeks, financially motivated assaults have additionally been noticed utilizing the Phorpiex (aka Trik) botnet malware propagated by way of phishing emails to ship the LockBit ransomware.
“In contrast to the previous LockBit ransomware incidents, the risk actors relied on Phorpiex to ship and execute LockBit ransomware,” Cybereason famous in an evaluation. “This method is exclusive as ransomware deployment normally consists of human operators conducting the assault.”
One other important preliminary an infection vector considerations the exploitation of unpatched VPN home equipment (e.g., CVE-2021-20038) to realize entry to inside community units and hosts and finally deploy Abyss Locker ransomware.
The assaults are additionally characterised by means of tunneling instruments to keep up persistence, in addition to leveraging Convey Your Personal Weak Driver (BYOVD) strategies to disable endpoint safety controls.
“After gaining entry into the surroundings and performing reconnaissance, these tunneling instruments are strategically deployed on important community units, together with ESXi hosts, Home windows hosts, VPN home equipment, and community hooked up storage (NAS) units,” Sygnia researchers stated.

“By concentrating on these units, the attackers guarantee strong and dependable communication channels to keep up entry and orchestrate their malicious actions throughout the compromised community.”
The ransomware panorama – led by risk actors new and outdated – continues to stay in a state of flux, with assaults pivoting from conventional encryption to information theft and extortion, whilst victims more and more refuse to pay up, resulting in a decline in funds in 2024.
“Teams like RansomHub and Akira now incentivize stolen information with massive rewards, making these ways fairly profitable,” cybersecurity agency Huntress stated.