Microsoft is asking consideration to an rising menace cluster it calls Storm-2372 that has been attributed to a brand new set of cyber assaults aimed toward a wide range of sectors since August 2024.
The assaults have focused authorities, non-governmental organizations (NGOs), data expertise (IT) companies and expertise, protection, telecommunications, well being, larger schooling, and power/oil and fuel sectors in Europe, North America, Africa, and the Center East.
The menace actor, assessed with medium confidence to be aligned with Russian pursuits, victimology, and tradecraft, has been noticed focusing on customers through messaging apps like WhatsApp, Sign, and Microsoft Groups by falsely claiming to be a distinguished individual related to the goal in an try to construct belief.
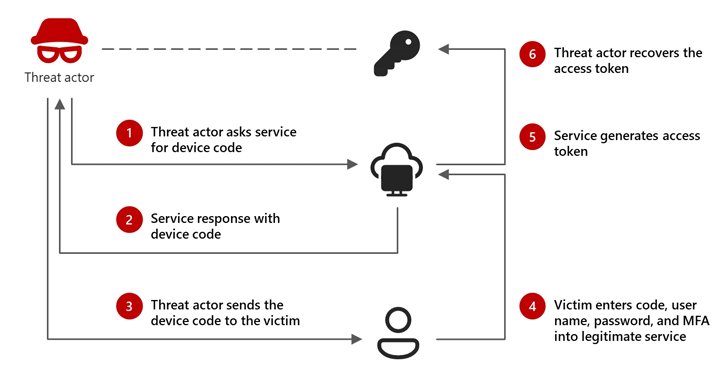
“The assaults use a selected phishing method referred to as ‘machine code phishing’ that methods customers to log into productiveness apps whereas Storm-2372 actors seize the data from the log in (tokens) that they’ll use to then entry compromised accounts,” the Microsoft Risk Intelligence mentioned in a brand new report.
The purpose is to leverage the authentication codes obtained through the method to entry goal accounts, and abuse that entry to pay money for delicate knowledge and allow persistent entry to the sufferer surroundings so long as the tokens stay legitimate.
The tech large mentioned the assault includes sending phishing emails that masquerade as Microsoft Groups assembly invites that, when clicked, urge the message recipients to authenticate utilizing a menace actor-generated machine code, thereby permitting the adversary to hijack the authenticated session utilizing the legitimate entry token.

“Through the assault, the menace actor generates a professional machine code request and methods the goal into getting into it right into a professional sign-in web page,” Microsoft defined. “This grants the actor entry and permits them to seize the authentication—entry and refresh—tokens which are generated, then use these tokens to entry the goal’s accounts and knowledge.”
The phished authentication tokens can then be used to realize entry to different companies that the person already has permissions to, similar to e mail or cloud storage, with out the necessity for a password.
Microsoft mentioned the legitimate session is used to maneuver laterally inside the community by sending comparable phishing intra-organizational messages to different customers from the compromised account. Moreover, the Microsoft Graph service is used to look by means of messages of the breached account.
“The menace actor was utilizing key phrase looking out to view messages containing phrases similar to username, password, admin, teamviewer, anydesk, credentials, secret, ministry, and gov,” Redmond mentioned, including the emails matching these filter standards have been then exfiltrated to the menace actor.
To mitigate the danger posed by such assaults, organizations are really helpful to dam machine code stream wherever attainable, allow phishing-resistant multi-factor authentication (MFA), and observe the precept of least privilege.
Replace
In an replace shared on February 14, 2025, Microsoft mentioned it “noticed Storm-2372 shifting to utilizing the particular shopper ID for Microsoft Authentication Dealer within the machine code sign-in stream.”
Utilizing the shopper ID, it added, permits the attackers to obtain a refresh token that can be utilized to request one other token for the machine registration service, after which register an actor-controlled machine inside Entra ID. The related machine is then used to reap emails.
“With the identical refresh token and the brand new machine id, Storm-2372 is ready to get hold of a Main Refresh Token (PRT) and entry a corporation’s sources,” Microsoft mentioned. “The actor has additionally been noticed to make use of proxies which are regionally applicable for the targets, seemingly in an try to additional conceal the suspicious sign up exercise.”
Cybersecurity agency Volexity mentioned it has noticed a minimum of three completely different Russian menace actors conducting spear-phishing campaigns utilizing the machine code method to compromise Microsoft 365 accounts since mid-January 2025.
A few of the emails have been recognized as despatched from accounts impersonating people from america Division of State, Ukrainian Ministry of Defence, European Union Parliament, and different distinguished analysis establishments.
One of many clusters behind the exercise is suspected to be APT29, which is also called BlueBravo, Cloaked Ursa, CozyLarch, Cozy Bear, Midnight Blizzard (previously Nobelium), and The Dukes. The opposite two teams have been assigned the monikers UTA0304 and UTA0307.

In a single occasion analyzed by Volexity, UTA0304 first approached a sufferer on Sign masquerading as an official from the Ukrainian Ministry of Defence, after which persuaded them to shift the dialog to a different safe chat utility referred to as Component.
The attacker proceeded to ship them a spear-phishing e mail, stating they wanted to click on on a hyperlink supplied within the message to hitch a chat room. Clicking the hyperlink redirected the sufferer to a Microsoft web page that asks for a tool code in an effort to “enable entry.”
“The message was a ploy to idiot the person into considering they have been being invited right into a safe chat, when in actuality they have been giving the attacker entry to their account,” Volexity’s Charlie Gardner, Steven Adair, and Tom Lancaster mentioned in an evaluation.
“The generated Machine Codes are solely legitimate for quarter-hour as soon as they’re created. In consequence, the real-time communication with the sufferer, and having them count on the ‘invitation,’ served to make sure the phish would succeed by means of well timed coordination.
CozyLarch and UTA0307, likewise, are mentioned to have adopted an identical technique, urging victims to hitch a Microsoft Groups assembly to realize unauthorized entry to the Microsoft 365 account, adopted by exfiltrating paperwork of curiosity.
“It ought to be famous that it’s attainable that is the work of a single menace actor working a number of, completely different campaigns,” the researchers mentioned, including they’re being tracked individually resulting from variations within the noticed parts.
“It seems that these Russian menace actors have made a concerted effort to launch a number of campaigns towards organizations with a purpose of concurrently abusing this methodology earlier than the targets catch on and implement countermeasures.”